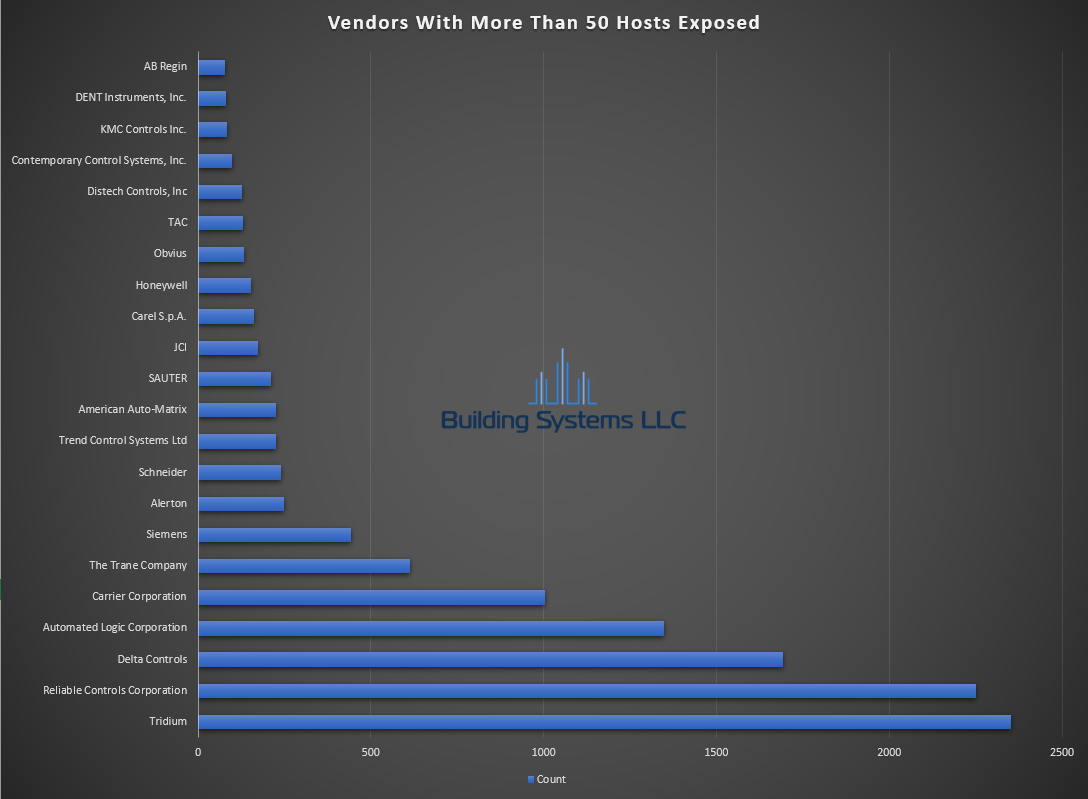
March ASOS summery below.
- Total Hosts with 47808 Exposed – 22,908
- Total BACnet Hosts – 12,604
- Total Unknown / Suspected BACnet- 1,084
- Total Unknown – 10,304
- Total Number of Vendors – 122

Providing custom solutions to the building automation industry.
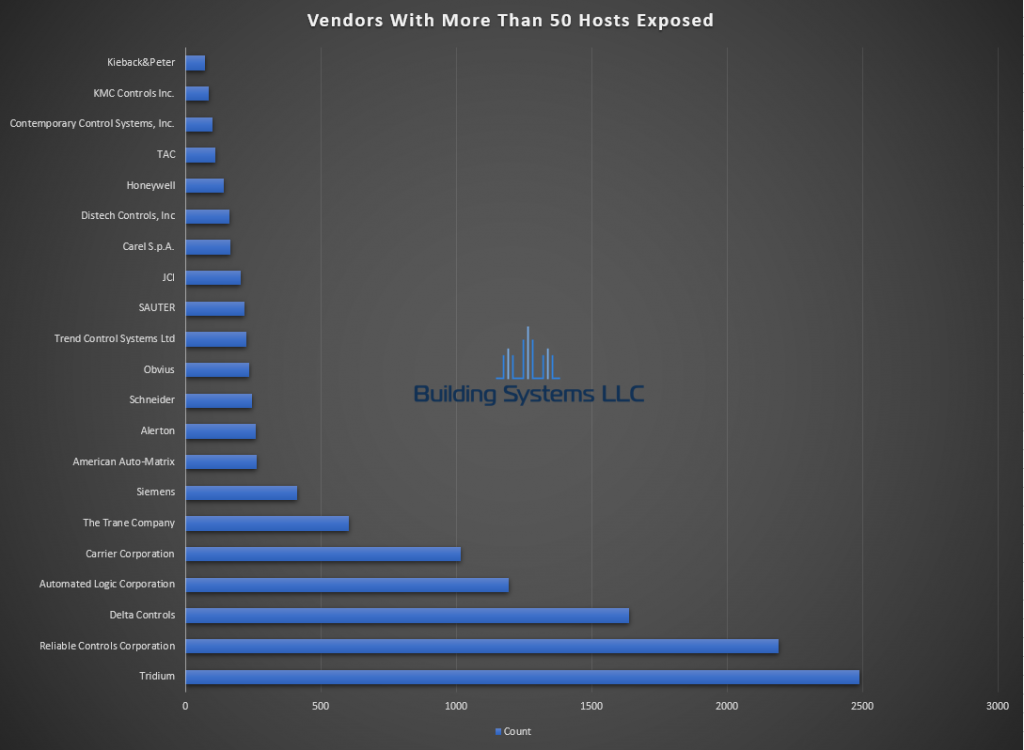
March ASOS summery below.


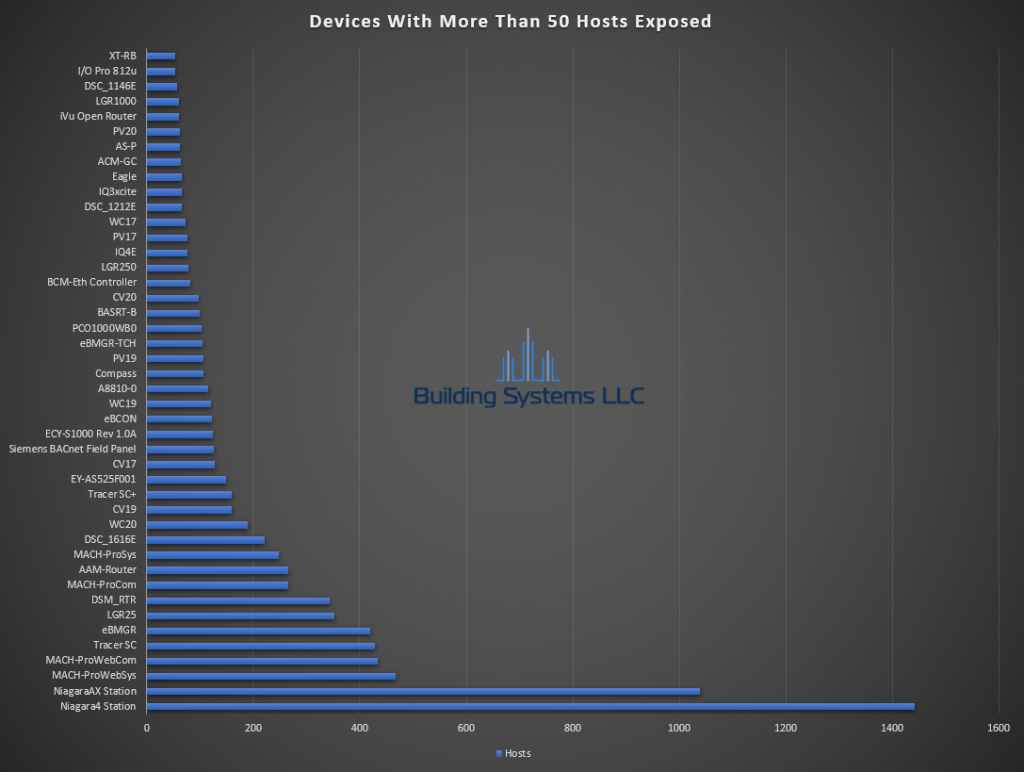
June ASOS summery below.
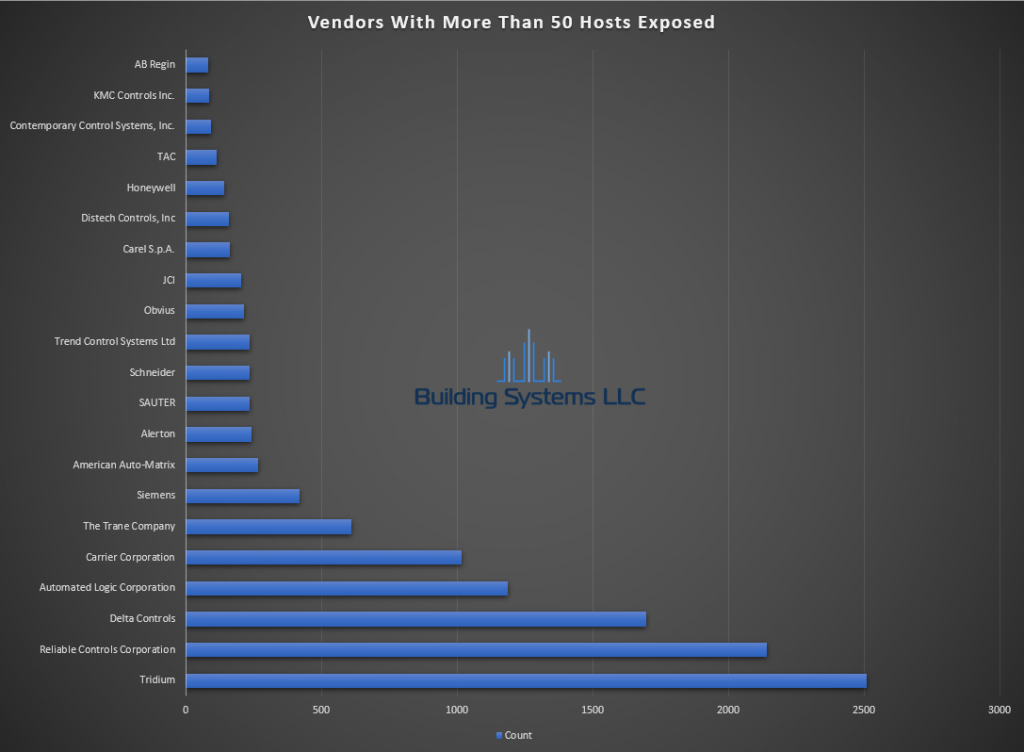
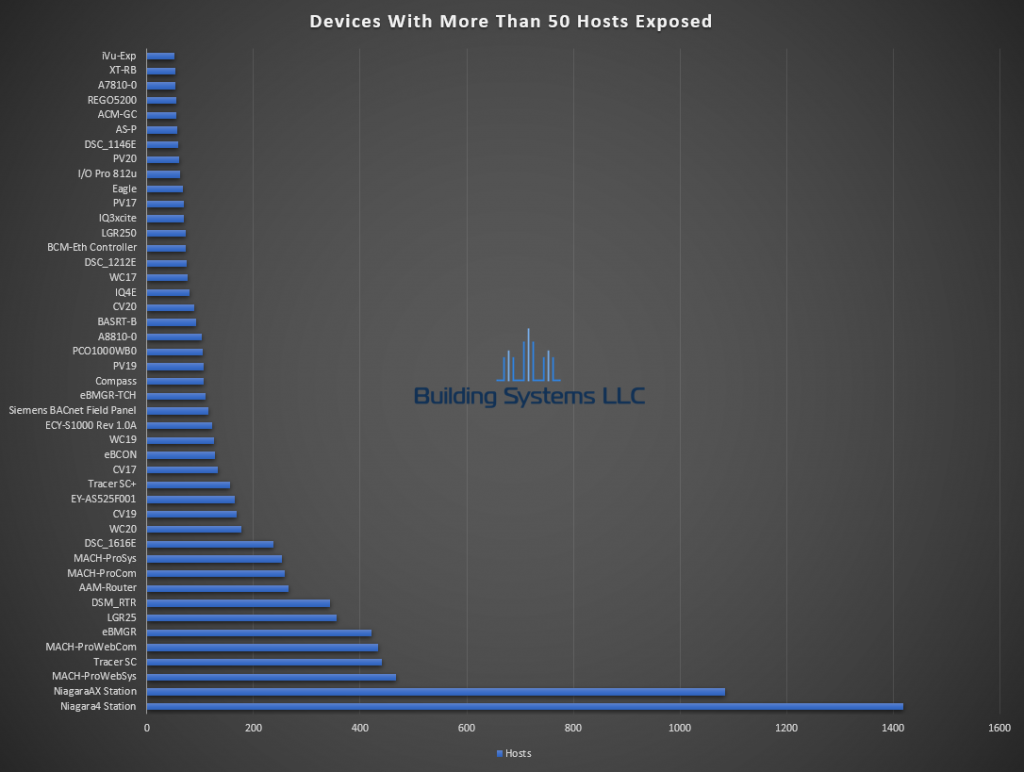
March ASOS summery below.
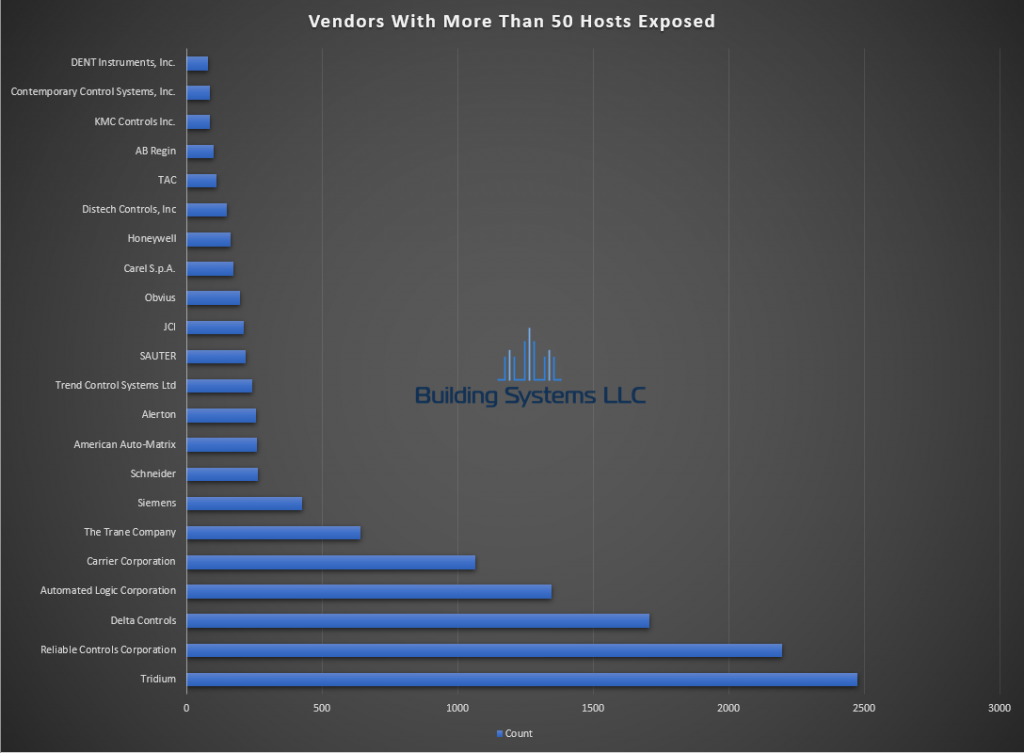
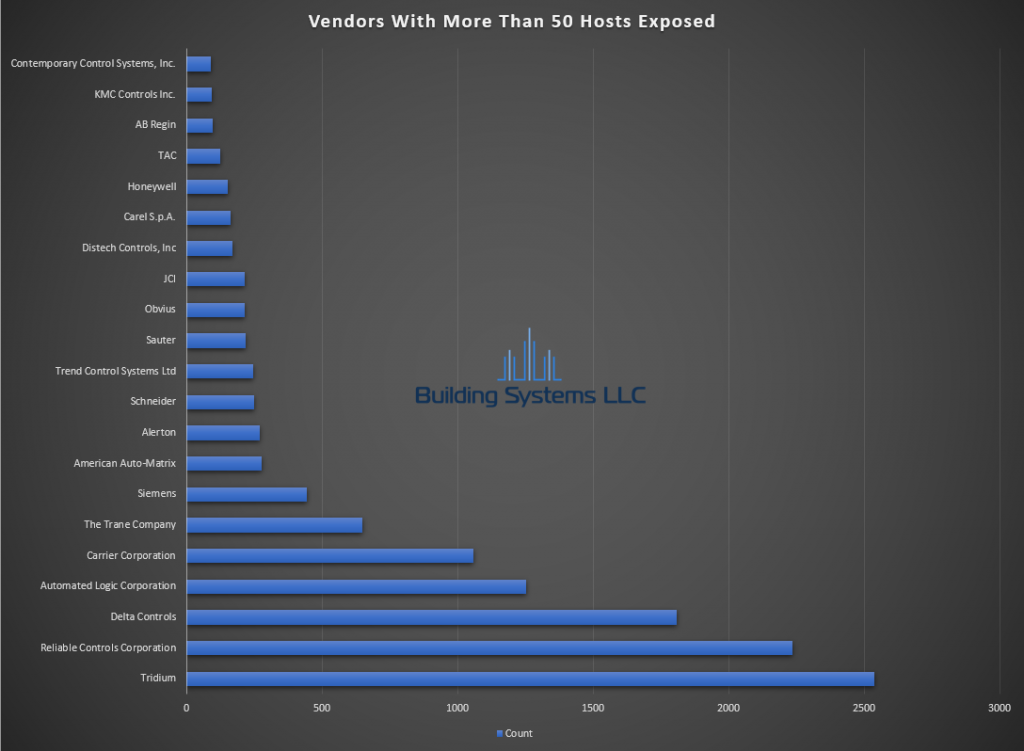
April ASOS summery below.
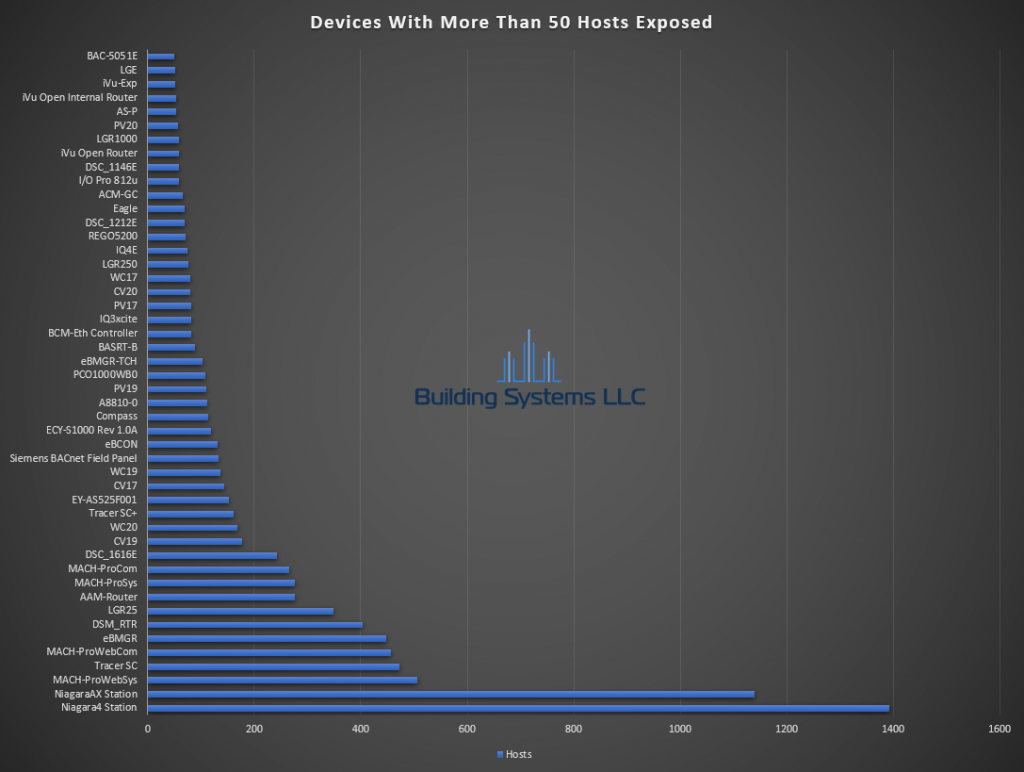
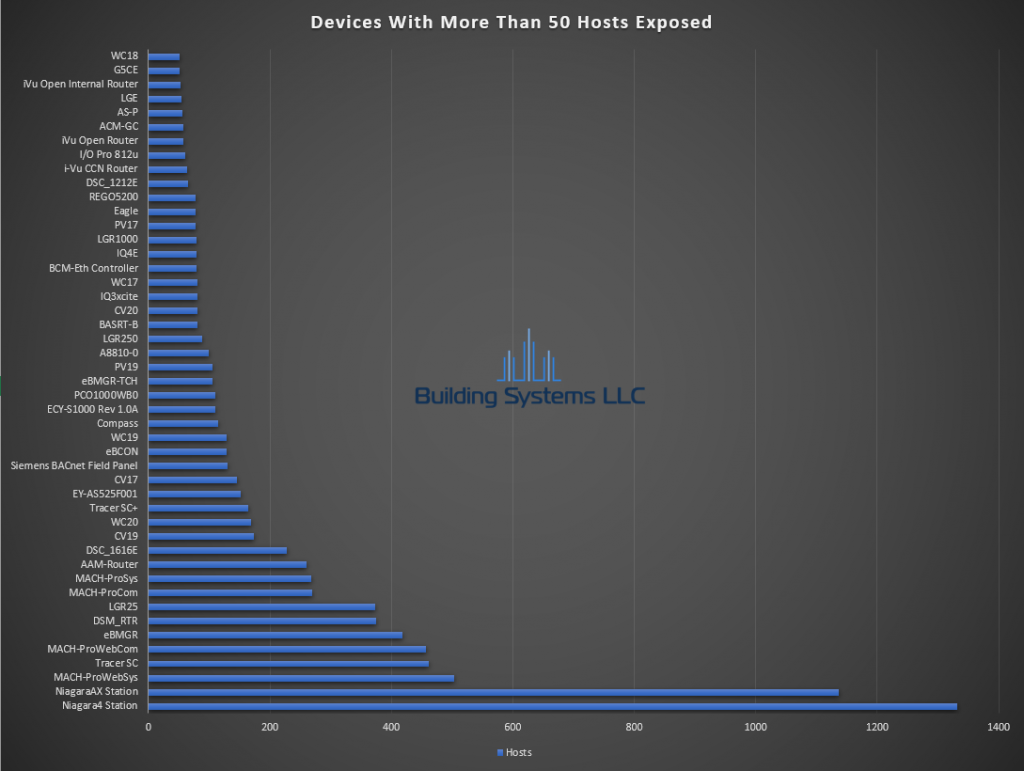
February ASOS summery below.
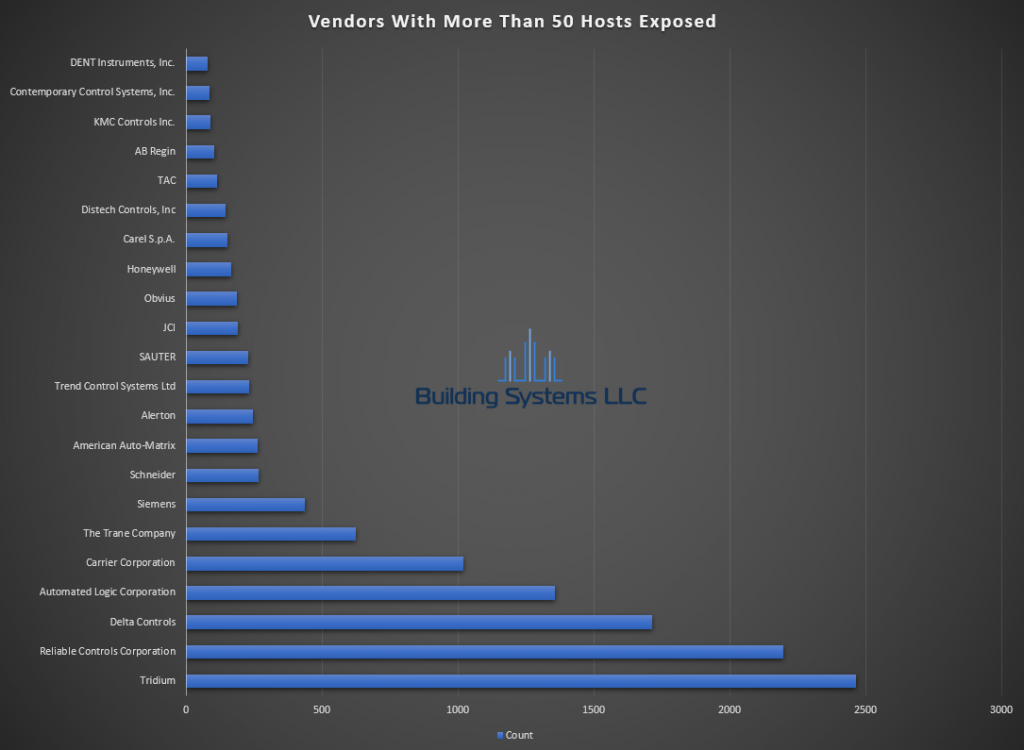
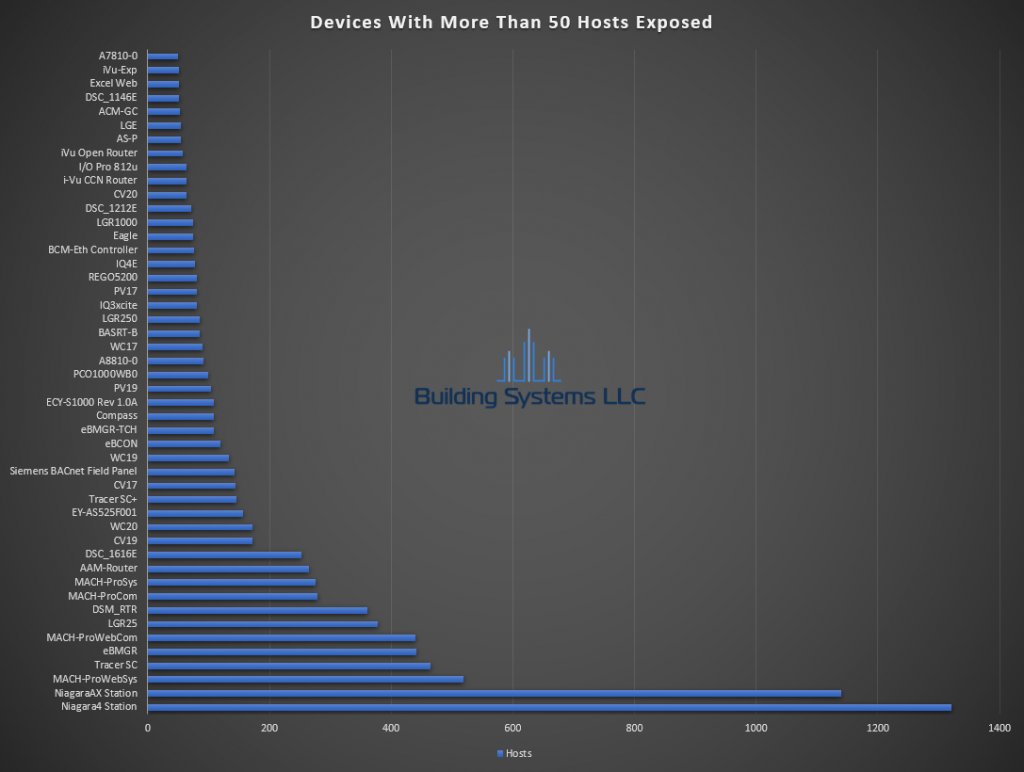
January ASOS summery below.
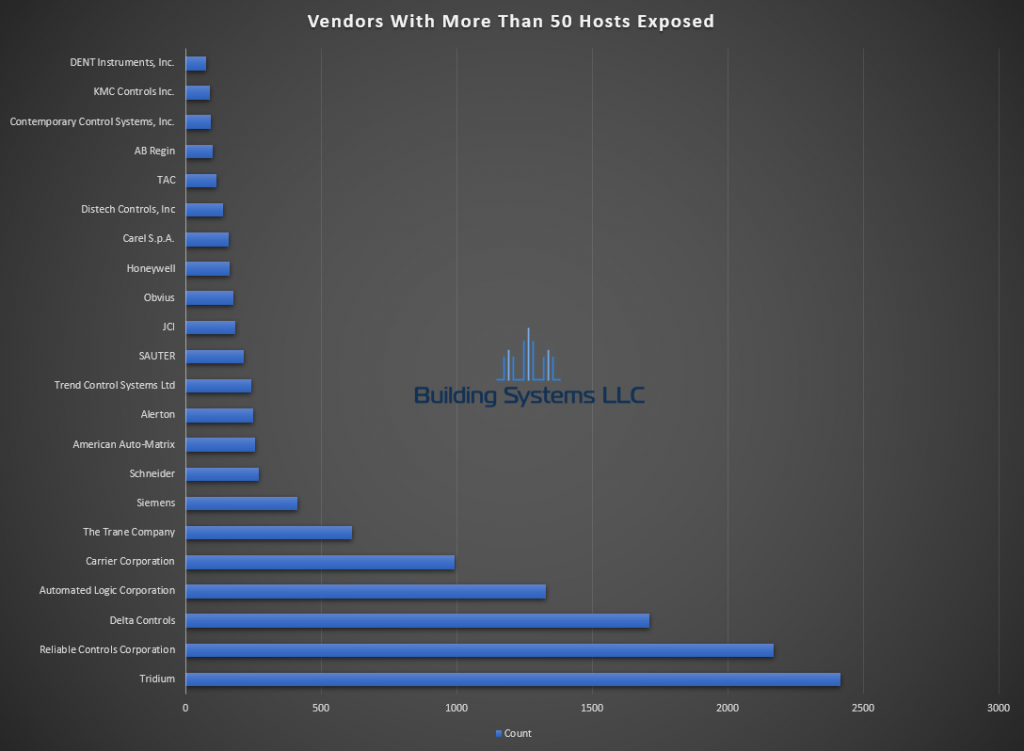
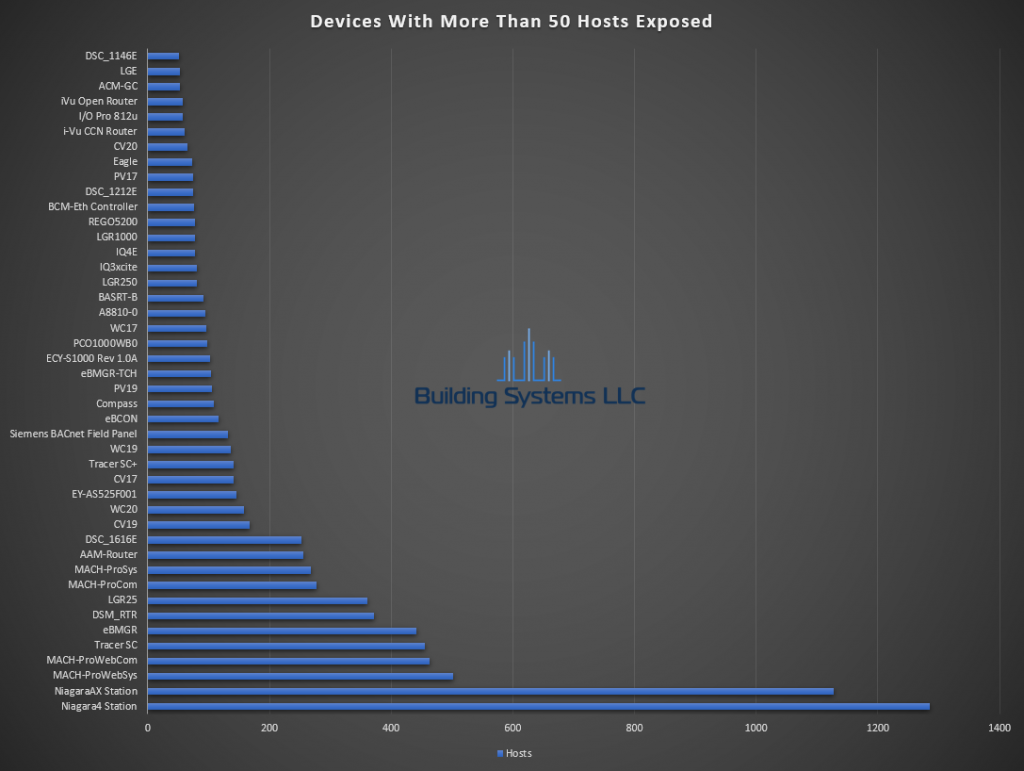
November ASOS summery below.
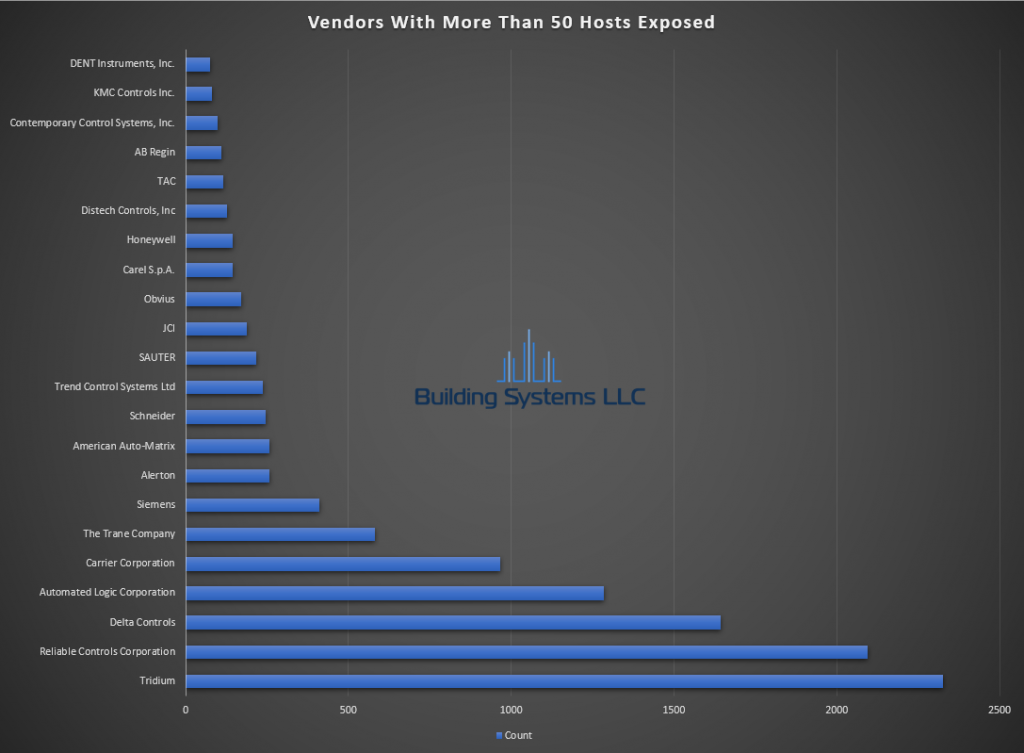
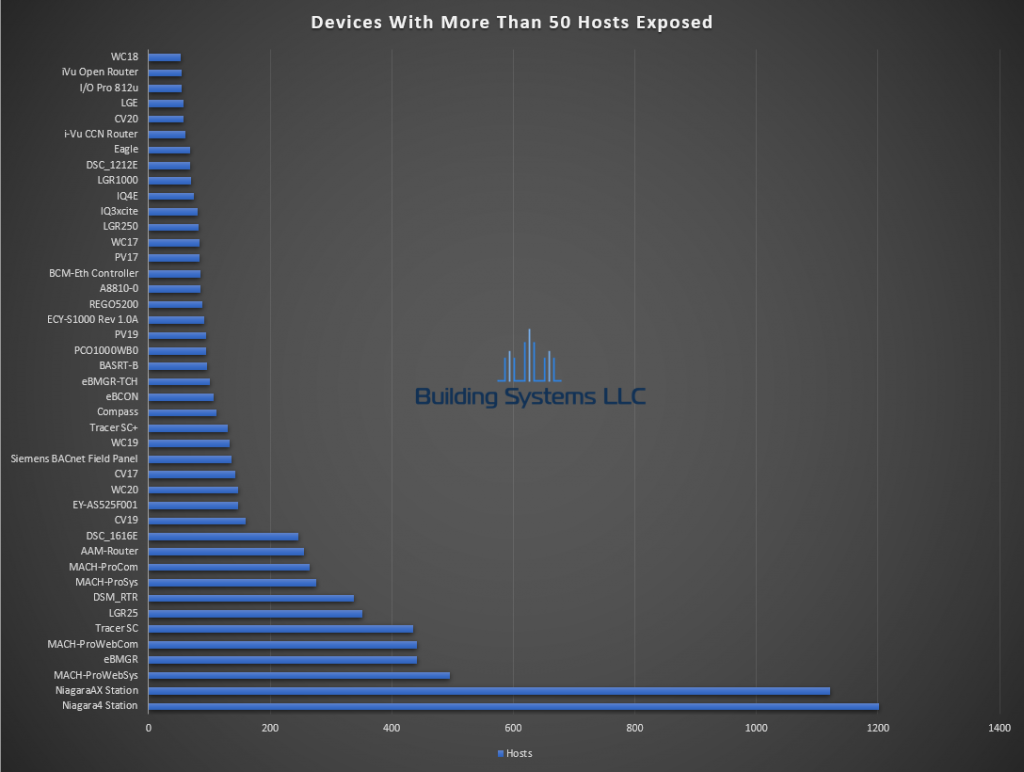
November ASOS summery below.

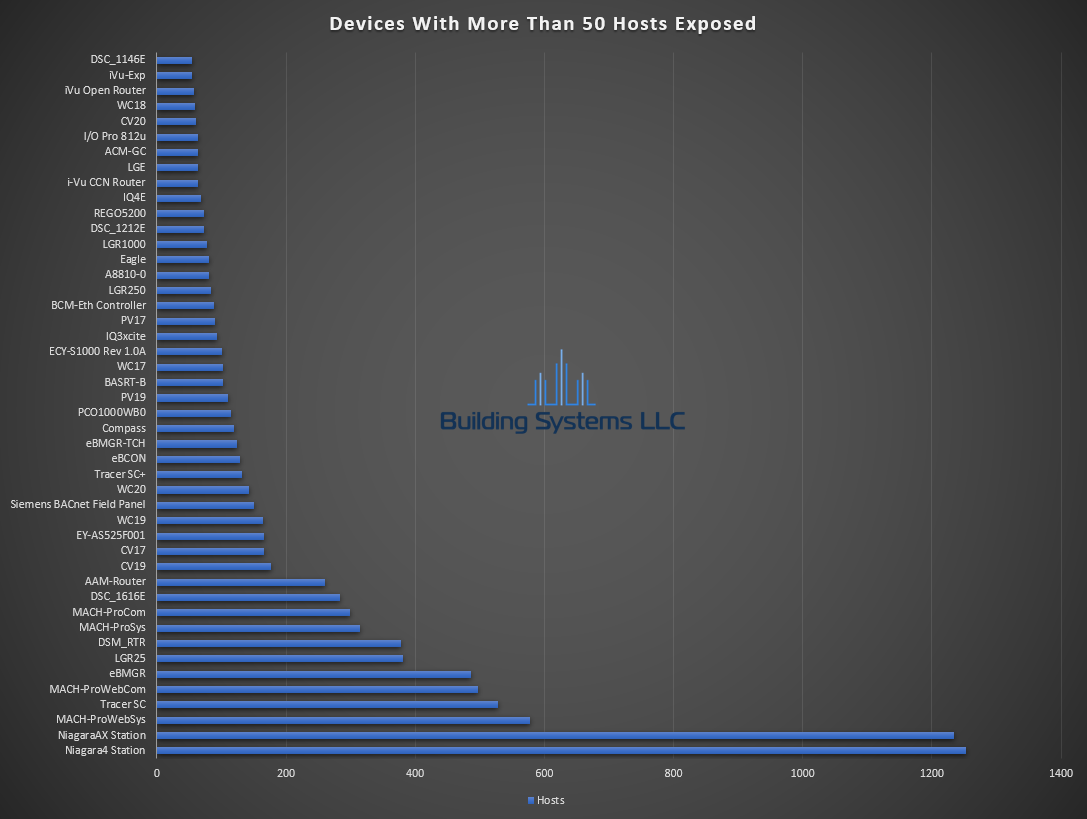
October ASOS summery below.
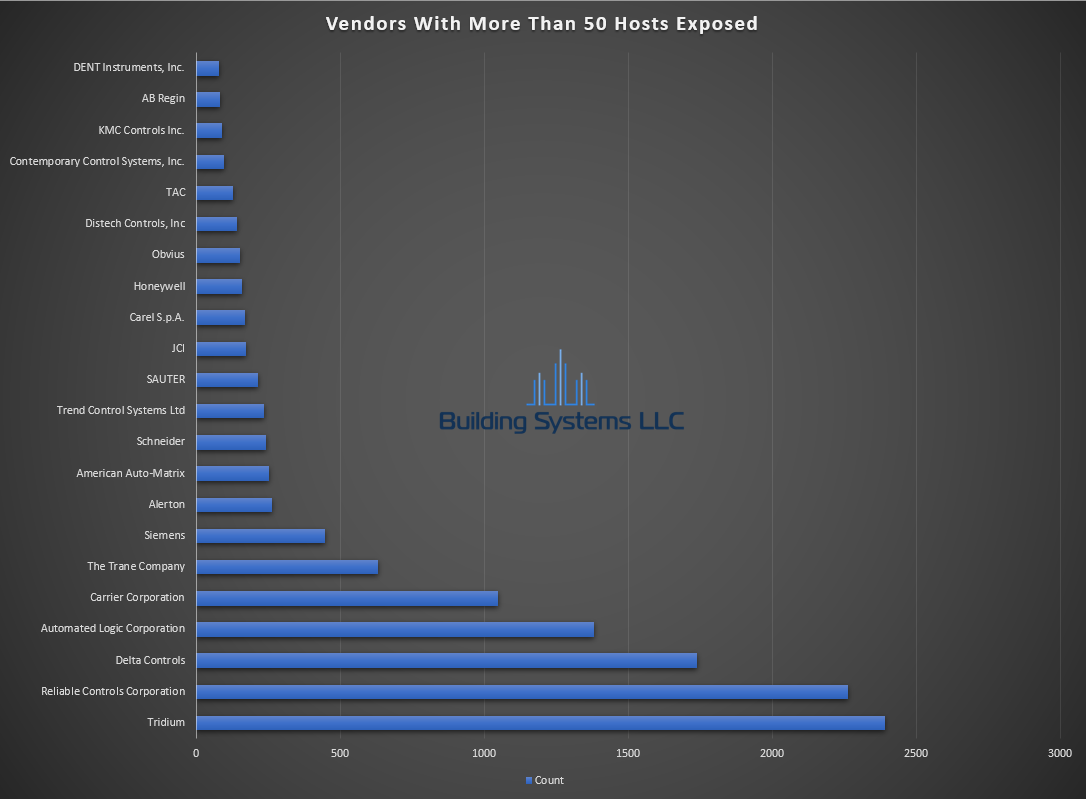
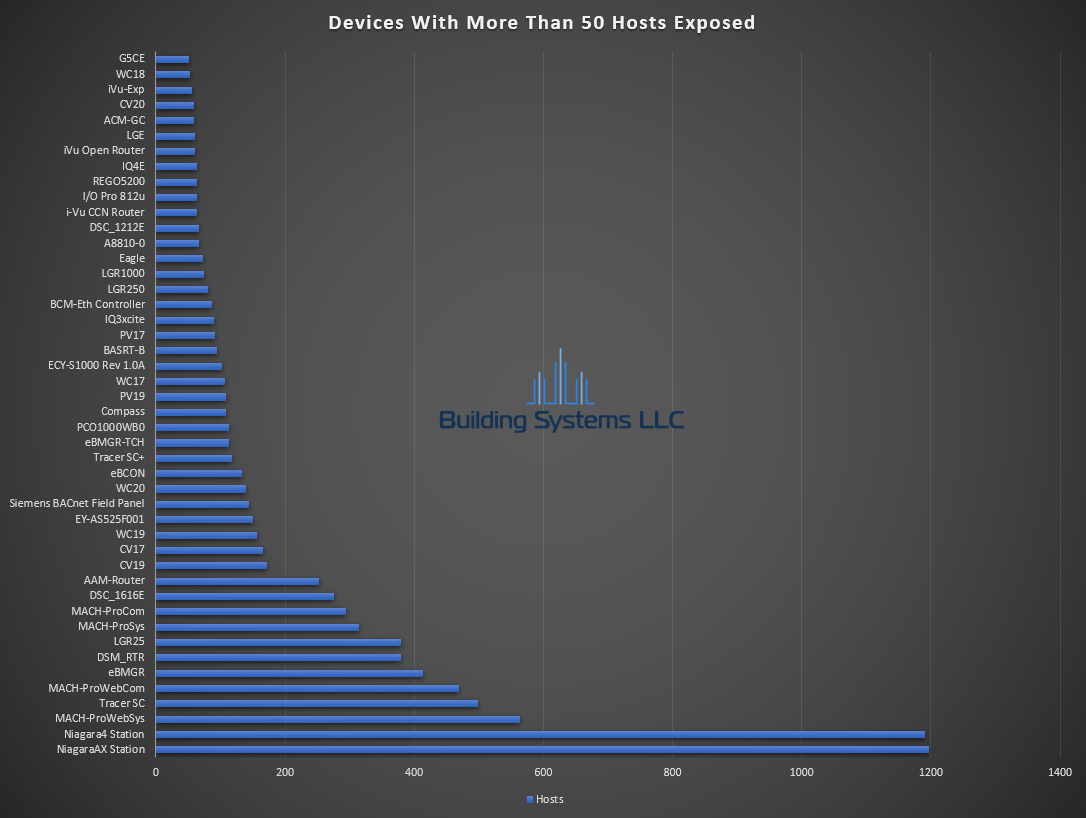
September ASOS summery below.