
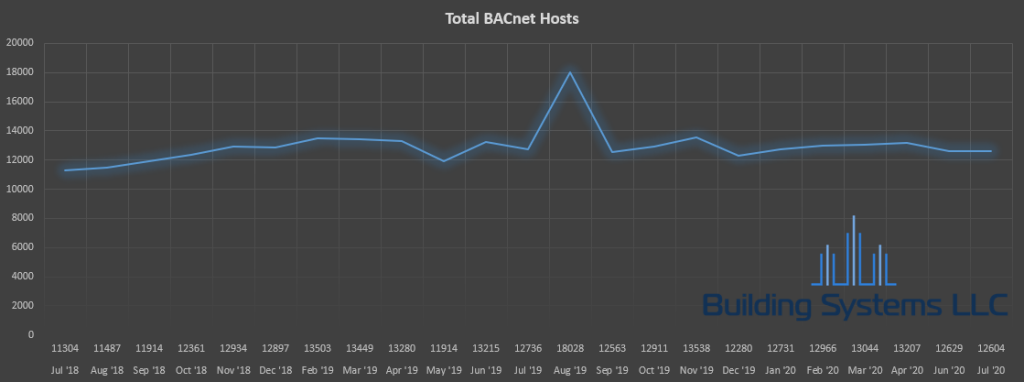
Ever wonder how many BACnet systems are exposed on the internet? This is an ongoing project to analyze BACnet hosts found in the Shodan database. Each month, results from Shodan hosts with port 47808 will be analyzed. Monthly reports will analyze results by vendor, device model and location.
Monthly Reports
- July 2018
- August 2018
- September 2018
- October 2018
- November 2018
- December 2018
- January 2019
- February 2019
- March 2019
- April 2019
- May 2019
- June 2019
- July 2019
- August 2019
- September 2019
- October 2019
- November 2019
- December 2019
- January 2020
- February 2020
- March 2020
- April 2020
- June 2020
- July 2020
Never Expose BACnet to the Public Internet
While the BACnet standard allowed for some basic level of security, nothing on the market today supports it. I’m told the BTL testing labs have also never certified a device supporting this to date. If someone can discover a device, they can start commanding objects and changing settings with freely available BACnet tools.
Results of exposing devices could range from annoying to real damage. Turning the heat off in during a winter holiday weekend, to downloading corrupt firmware / program files bricking devices.
If remote access is required its extremely important to either use VPNs or more secure protocols to transit the public internet.
Report Details
Shodan’s report contains the IP address, banner, timestamp, host name, and location based on the IP address. For BACnet hosts that respond, the banner will contain the instance, object name, device location, vendor name, BDT table, application / firmware version, device model and name.
Our scripts parse Shodan’s banners to do some basic classification on the host. Hosts that responded with valid responses are considered BACnet devices. Unknown hosts are hosts that either have invalid BACnet responses, BACnet error messages, or empty banners. Hosts that reply with a BACnet error message are considered Unknown / Suspected BACnet devices.
After classifying the hosts, they are sorted and the occurrence each vendor and device model is calculated. Since some control vendors have identity crises requiring additional filtering. Honeywell for example uses “Honeywell”, “Honeywell International, Inc” and “Honeywell International Inc.”. Vendor names reduced to alpha numeric characters with spaces removed when calculating vendor totals. Additional rules look for the first occurrence of a vendor known to use multiple different names and all further occurrences of any variation are counted together.
Additional BACnet Security Research
- BACnet WAN Security Threat Assessment
- Public BACnet Devices for DDOS
- Analysis of Security Issues in Building Automation Systems
Public BACnet Scanning
There are several other actors constantly scanning the internet for BACnet devices. Using honeypots we regularly see scans from the following organizations as well as other unidentified sources.
BACnet Secure Connect
Secure Connect (BACnet/SC) may solve the security issues surrounding BACnet and is currently working through the approval process. SC uses TLS between devices, eliminates the need for BBMDs and static IPs. Final approval is expected to happen sometime in late 2019. How long it takes for manufactures to implement and release products supporting it, is anyone’s guess. It will likely be many years yet before we see widespread adoption. SC could also turn into another form of vendor lock in.
BACnet/SC White Paper
Current BACnet/SC proposal under public review
11-19 Update BACnet/SC is officially approved
